Event and Log analysis
Common Security Events, how to analyze them, and the tools to do so
Types of data we work with
These are the parsed and normalized version of the log information that comes into your SIEM. These will help you be able to search for data in specific fields, create use cases that map across log sources, and provide the next level of detail beyond what appears in an alert.Event data - This is the data behind the alert. This should be all of the available details found in the reporting log file, normalized/converted into a standard format. This normalization is key, as it is what allows your searches to work across multiple log types. Generally, if you are working out of a SOAR or SIEM, you will be dealing with event data.When investigating an event, alert, or incident, there will be three levels of data you will look at:
Alert data - These are essentially searches made in your data to look for specific matches. If working out of an alert queue like most security analysts, this is what you will get first. The alert should show you the search logic as well as the data points that are matched in the search.
Event Data - These are the event logs that your searches and use cases work off of. They are typically normalized for processing by your SIEM, parsed so you know which fields you need, and possibly filtered to limit the scope of the data you might find relevant.
Log data - This is the raw, unedited, un-normalized data, before it is processed by another tool. Generally if you are working with an EDR platform, application logs, or system logs, these will be giving you raw log data.
Alert data and Event data can change depending on the platform you are using. Log data and format will be specific to the type of log that is being generated. Security analysts will typically be working from Alert/Event data, and then pivot to log data if they need further investigation. Threat hunters and forensics investigators will typically use raw log data for its granular level of detail.
Understanding Log results and thier contents
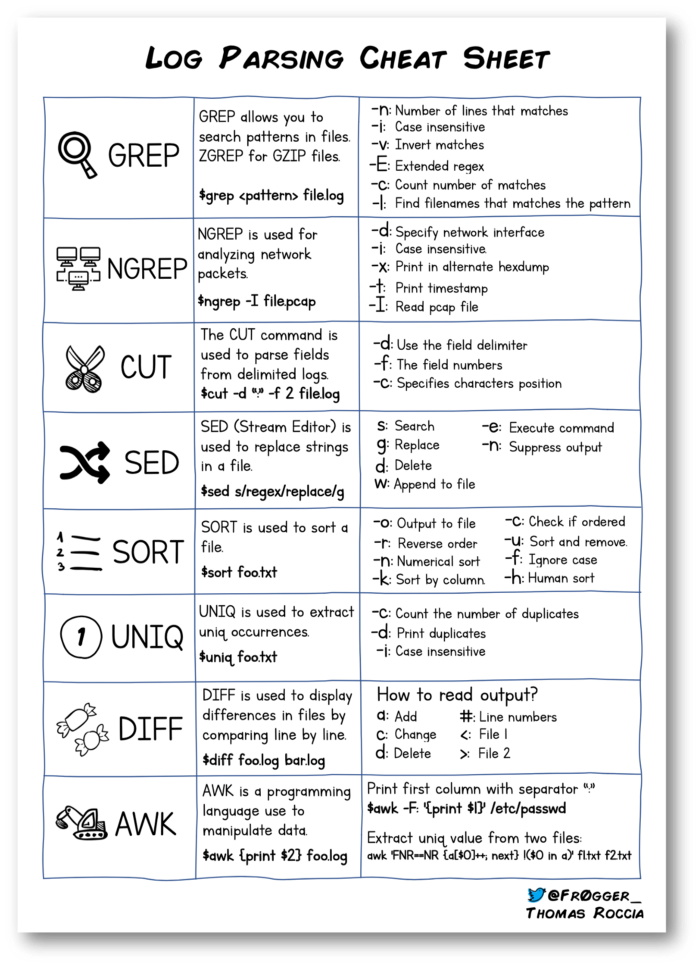
Logging formats will change depending on the log, log source, application, and manufacturer. Most are super dense with information and can be difficult to parse with out any reference. Below are some collections of cheatsheets and tool outputs that can help you make sense of some of the log types you might deal with and part of an investigation.
Platform Logs
https://what2log.com/ - What2Log is an amazing platform that breaks down the different logs and data points found within those logs, and gives fantastic guidance on what exactly they mean.
Cheat-Sheets — Malware Archaeology - Collection of logging cheatsheets for various windows log types.
Linux Logs Explained - Full overview of Linux Log Files - Plesk - Breakdown of the files and paths of the various logs created by Linux
Windows Security Log Encyclopedia - Explanation of Windows Event IDs
Windows Security Identifiers - Describes security identifiers and how they work in regards to accounts and groups in the Windows operating system.
What are Azure Active Directory reports? | Microsoft Docs - Understanding Azure AD Audit logs
Sign-in log schema in Azure Monitor | Microsoft Docs - Understanding Azure sign-in logs
Detailed properties in the audit log - Microsoft 365 Compliance | Microsoft Docs - O365 Log breakdown
Protocol Specific Logs
Understanding DHCP Server Log File Format - DHCP log breakdown
The Importance of DNS Logging in Enterprise Security - DNS log fields and analysis
Tool/Application Logs
Tool Analysis Result Sheet - Great collection of tool outputs collected by the JP-CERT.
Microsoft Defender AV event IDs and error codes | Microsoft Docs - Understanding Defender AV event codes and Defender logs
Sysmon - Windows Sysinternals | Microsoft Docs - Breakdown of sysmon logging and reported events.
Proxy server logs for incident response - Web Proxy log breakdown
File properties and metadata
Strontic xCyclopedia - Huge encyclopedia of executables, dll files, scripts, even the file paths they are supposed to be under. Contains tons of metadata, file hashes, reputation scores, handles, and so much more!
Winbindex - Index of windows binaries with file hash, size, what update it was created with, and many more. Perfect for understanding more on a file.
Echotrail.io - A super handy tool that maps windows file to hashes, parent/child process, and much more. Great for determining if a file is really is a windows file, or is behaving in a way that it should.
https://www.systemlookup.com/ - SystemLookup hosts a collection of lists that provide information on the components of legitimate and potentially unwanted programs.
https://filesec.io/ - Stay up-to-date with the latest file extensions being used by attackers.
Misc
https://malapi.io/ - Cheatsheet for commands that could be potentially used for malicious activity.
Reference
BTFM: Log Auditing - pg. 51
Crafting the InfoSec Playbook: Logging Requirements - pg.48
Cyber Operations: Logging - pg. 455
Last updated