Threat Hunting
Intro
Threat hunting doesn’t have to be complex, but it’s not for everyone. Knowing how to begin and end a hunt is more important than knowing how to carry out a hunt. If you need a place to start, look at trends in the threat landscape and focus on threats that you do not have automated alerts/detections for. Hunting is a creative process that rewards those who take chances. Finish with something, anything actionable — so long as it provides value.
Guides and Reference
Threat Hunter Playbook - a community-based open source project developed to share threat hunting concepts and aid the development of techniques and hypothesis for hunting campaigns by leveraging security event logs from diverse operating systems.
huntpedia.pdf - Book written by seasoned threat hunters on thier techniques and theory.
Open Threat Research Forge - Github repository of Threat Hunting articles, playbooks and tools.
ACM's Threat Hunting Labs - These are a series of labs that cover different types of analysis that can be done on network data when threat hunting.
HowToHunt - Tutorials and Things to Do while Hunting Vulnerability.
ThreatHunting Home - Links and Blog on popular threat hunting proceedures
Tool Analysis Result Sheet - JP-CERT analysis on detecting the use of multiple popular tools within an network environment.
https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE5aC6y?culture=en-us&country=US - Microsoft's Threat Hunting Survival Guide
https://drive.google.com/file/d/14DluguBRjlUt9GWTUpGIB802qnHD2Olp/view - Introduciton to Threat Hunting part 1
Tools
RedHunt-OS - Virtual Machine for Adversary Emulation and Threat Hunting by RedHunt Labs
ThreatPursuit-VM - A fully customizable, open-sourced Windows-based distribution focused on threat intelligence analysis and hunting designed for intel and malware analysts as well as threat hunters to get up and running quickly.
Splunkhunting
Hunting Theory
Types of Hunts - **This will cause some disagreement amongst threat hunting theorists, but this is the common thought process.** There are 3 types of hunts:
Automated - IoC ingest, should be performed by your SIEM and SOAR
Continuous - Situational awareness and Behavioral analytics. If these can be turned into alerting searches, all the better. Otherwise these should be scheduled at reasonable intervals.
On demand - Looking for specific activity. This typically has a temporal element such as responding to given intelligence.
3 types of Hunt hypothesis
Threat Intelligence - These are hunts for specific indicators. These are easy low handing fruit, and should be followed by adding the indicators to any alerting mechanisms present.
Situational Awareness - These hunts are for looking at normal system and network operations and identifying activity that is outside of normal operations. This can include changes in volume/frequency of events, the methodology of certain activities, or the specific data points associated with certain events.
One of the biggest threat hunting skills is not only seeing what data doesnt belong, but also see what data is missing.
Domain Expertise - This is one that requires specific knowledge of your local environment. These hunts look for similar items as Situational Awareness, with the added context of looking for oddities in your specific organizations operations. Many of these will be violations of corporate policy or local practice and standards.
Hunt determinations
Can this hunt be automated?
Can this hunt be repeatable?
Are the indicators in this hunt monitored by other services?
Are we already hardened against these indicators?
Hunting Strategy questions:
What are you hunting?
Where will you find it?
How will you find it?
When will you find it?
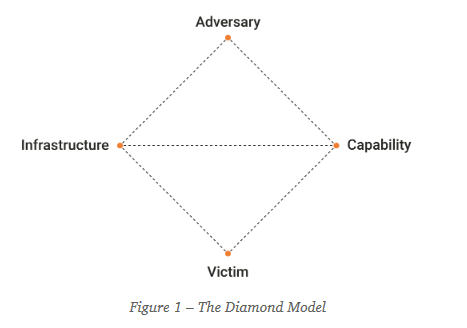
*Ask these questions from each point int he Diamond Model
Threat Hunting with Elastic Stack - pg. 29
Techniques
Repeatable hunts
These are hunt theories and searches that can and should be performed on the regular.
Long Tail Analysis
https://www.ericconrad.com/2015/01/long-tail-analysis-with-eric-conrad.html
Crown Jewel Analysis
Preparing for CJA requires organizations to do the following:
Identify the organization’s core missions.
Map the mission to the assets and information upon which it relies.
Discover and document the resources on the network.
Construct attack graphs. → Determine dependencies on other systems or information. → Analyze potential attack paths for the assets and their interconnections. → Rate any potential vulnerabilities according to severity.
This type of analysis allows hunters to prioritize their efforts to protect their most tempting targets by generating hypotheses about the threats that could impact the organization the most.
Crown Jewel Analysis - Crafting the Infosec Playbook: pg. 21
Misc
https://github.com/schwartz1375/aws - Repo for threat hunting in AWS.
Last updated