Domain
Domains
A domain name is a string that identifies a realm of administrative autonomy, authority or control within the Internet. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name identifies a network domain or an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, or a server computer. Domain names are often used to identify services provided through the Internet, such as websites and email services
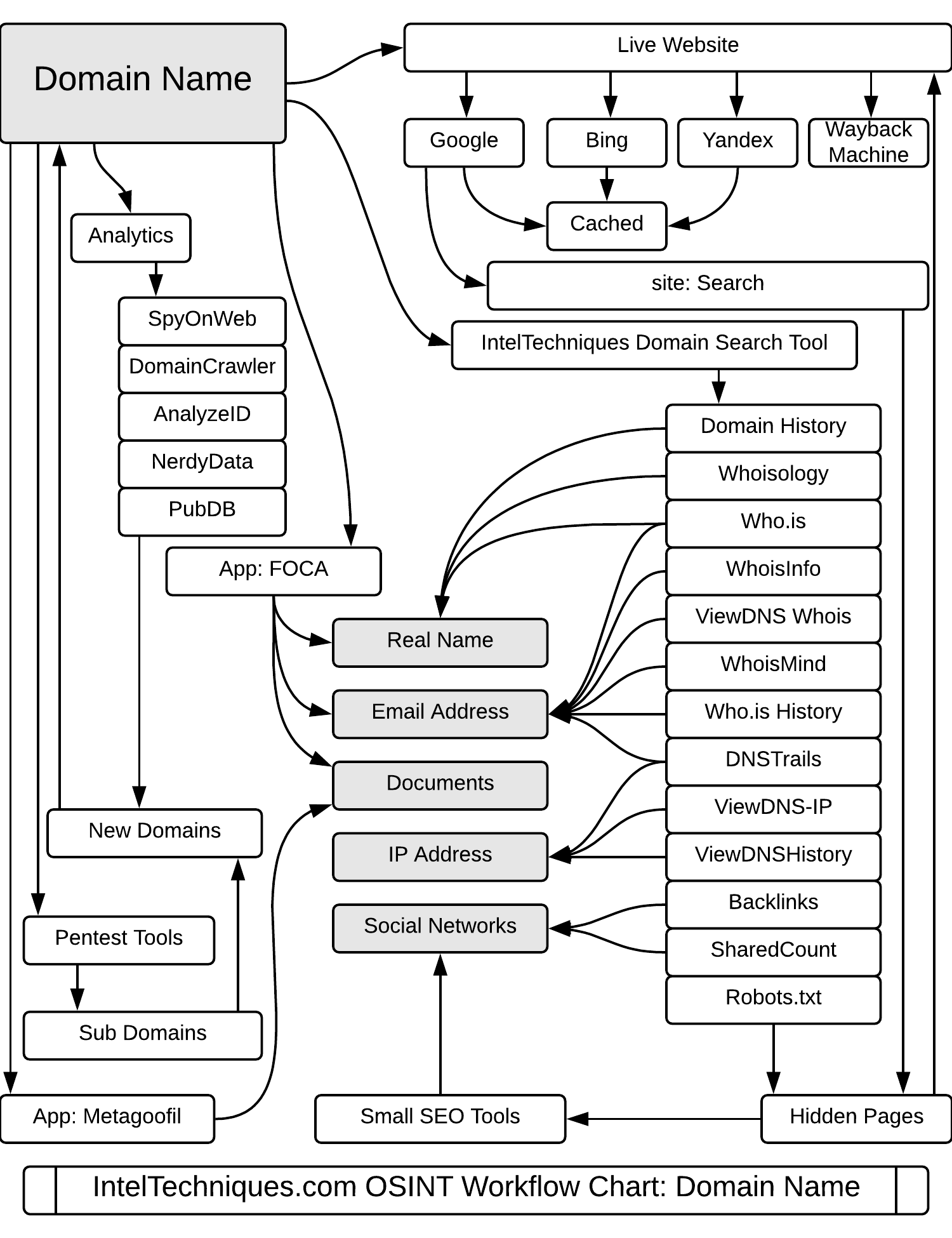
Domains, more than almost any other target, have one of the largest assortments of associated data points. The most important that we will look for out of this section is the Registration data, the hosting data, site information, archived data, and analytics.
Whois Vs. RDAP
Whois is a great tool for gathering registration data for IP addresses and domains. The only problem with it is that there is not a clearly defined structure to organize registration data points and keep them maintained. Enter RDAP. A new Standard as of 2019, RDAP lookups will quickly replace WHOIS lookups.
RDAP lookup tool - https://client.rdap.org
General information on RDAP - https://www.icann.org/rdap
Domain Analysis Tools
Domain.html
Domain.html is a tool that allows us to research multiple data points associated with a domain that might be handy during an investigation.
Registration Data - This tool will check the domain for whois based registration data against multiple sources to get the most up to date data.
Hosting Data - This is the information that shows which provider is physically hosting the domain. Be sure to look for indicators if the target domain is hosted by a hosting provider, or self hosted by your target.
Exposed Data - Any information that may be exposed to the public. (Other sources are better)
Archive Data - When researching a domain, sometimes you can find older cached or saved versions of the website that may yield valuable information. These include Google Cache, Archive.is, and the WayBack Machine.
Analytics data - This is a grab bag of handy searches, ranging from general site details and analytics, to similar sites on the web, or checks for backlinks to from other sites.
Threat Data - Discussed under the Blue - Threat Data section
Shortened URL metadata.
Domain Toolboxes
These next few tools are collections of utilities focused around domains. Some can be used for research on other network artifacts like IP addresses and email records, but DNS records and domain related metadata is really where they shine.
ViewDNS - Huge toolbox with various utilities for enumerating information about a domain.
DNSDumpster - Free domain research tool that can discover hosts related to a domain.
MXToolbox - Checks MX information for the given domain
W3DT - W3dt.Net is an online network troubleshooting site dedicated to providing relevant real-time data regarding networks, websites and other technical resources.
DNSLytics - Find out everything about a domain name, IP address or provider. Discover relations between them and see historical data. Use it for your digital investigation, fraud prevention or brand protection.
HostSpider - Command line tool that gathers tons of information about a domain including DNS records, subdomains, WHOIS, Cloudflare IP, and more!
Sub-domain Discovery
There are tons of highly effective tools for subdomain enumeration and brute forcing, but they can be quite noisy. During the Passive Recon phase of a penetration test, we can start with any subdomains recorded by other sources to plan out our attack/test.
https://omnisint.io/ - Project Crobat: Rapid7's DNS Database easily searchable via a lightening fast API, with domains available in milliseconds.
censys-subdomain-finder - This is a tool to enumerate subdomains using the Certificate Transparency logs stored by Censys.
ctfr - Abusing Certificate Transparency logs for getting HTTPS websites subdomains.
Sublist3r - Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS.
puredns - Puredns is a fast domain resolver and subdomain bruteforcing tool that can accurately filter out wildcard subdomains and DNS poisoned entries.
Domain Certificates
Domain Certificates are an interesting and useful item to research when mapping out a target domain. Beyond the various attacks that can be performed by exploiting these certificates, looking up the domain certificates can lead to discovery of hosts, sub-domains, and related targets that were previously undiscovered.
Crt.sh - Enter an Identity (Domain Name, Organization Name, etc), a Certificate Fingerprint (SHA-1 or SHA-256) or a crt.sh ID to return detailed domain and certificate information.
CTSearch - Certificate Transparency Search Tool
tls.bufferover.run - Quickly find certificates in IPv4 space
CertSpotter - Monitors your domains for expiring, unauthorized, and invalid SSL certificates
SynapsInt - The unified OSINT research tool
Censys - Certificates - Certificates Search
PassiveTotal - Security intelligence that scales security operations and response
Google Transparency Report - A tool used to look up all of a domain’s certificates that are present in active public Certificate Transparency logs
https://sslmate.com/labs/ct_policy_analyzer/ - Certificate Transparency Policy Analyzer
Web Site Change Tracking
Some times a target will change a website and you will want to be notified right away, usually to see what has changed and how you can exploit it.
Follow that page - Follow That Page is a change detection and notification service that sends you an email when your favorite web pages have changed.
Visual Ping - Tool that can track multiple different kinds of changes in a particular webpage and alert on specific conditions.
URL Shortening and Redirections
https://shorteners.grayhatwarfare.com - search URL Shorteners
urlhunter - a recon tool that allows searching on URLs that are exposed via shortener services
https://checkshorturl.com - Get information about a shortened link
http://redirectdetective.com/ - Where does this redirection go?
https://wheregoes.com - Redirection link enumeration tool
https://lookyloo.circl.lu - Redirection link enumeration tool
How to check a short link instead of being redirected:
bit.ly - add + at the end
cutt.ly - add @
tiny.cc - add =
tunyurl.com - add "preview." to the beginning of the url.
Similar Web Site Search
https://www.similarsites.com/ - Enter a website URL and view websites that are similar.
https://siteslike.com/ - Enter a URL or keyword and view websites that are similar or match your keyword
https://www.similarweb.com/ - A great tool for finding similar and/or competitor websites. Search via website URL.
Browser Proxy/Simulator
For when you want to look at a site, without interacting with it.
https://www.wannabrowser.net/ - With Wannabroser you can have a look at the HTML-source code of any website from the view of any User-Agent you like. It's even possible to detect simple cloaking using Wannabrowser if the cloaking is just based on the visiting User-Agent.
https://www.browserling.com/ - Used for browser testing, but can be used for safely looking at various sites.
https://www.url2png.com/ - Capture snapshots of any website
Misc. Utilities
DNPedia - Domain Name Solutions, Statistics, Scripts, News and Tools
https://riddler.io/ - Obtain network information from F-Secure Riddler.io API.
Google's Online Dig command - Online version of the Dig command
SimilarWeb Traffic Analytics - Compare meta data about domains and traffic to other elements on the web
Backlink Checker - Tool to easily monitor backlinks for a particular domain.
DomLink - DomLink is a tool that uses a domain name to discover organization name and associated e-mail address to then find further associated domains.
https://dfir.blog/unfurl/ - Easily breakdown and visualize the elements of a URL link.
r3con1z3r - R3con1z3r is a lightweight Web information gathering tool with an intuitive features written in python. it provides a powerful environment in which open source intelligence (OSINT) web-based footprinting can be conducted quickly and thoroughly.
emailharvester - A tool to retrieve Domain email addresses from Search Engines.
https://github.com/lc/gau - getallurls (gau) fetches known URLs from AlienVault's Open Threat Exchange, the Wayback Machine, and Common Crawl for any given domain. Inspired by Tomnomnom's waybackurls.
lbd - Checks if a given domain uses load-balancing.
Metagoofil - Tool for extracting metadata out of public documents.
https://www.giftofspeed.com/cache-checker/ - This tool lists which web files on a website are cached and which are not. Furthermore it checks by which method these files are cached and what the expiry time of the cached files is.
CloudFlair - Find origin servers of websites behind CloudFlare by using Internet-wide scan data from Censys.
cf-check - Check an Host is Owned by CloudFlare.
AnalyticsRelationships - Get related domains / subdomains by looking at Google Analytics IDs
https://lots-project.com/?s=09 - Attackers are using popular legitimate domains when conducting phishing, C&C, exfiltration and downloading tools to evade detection. The list of websites below allow attackers to use their domain or subdomain.
Investigation Mind Maps
Last updated