YARA
Virustotal's file scanning engine and ruleset
What is Yara?
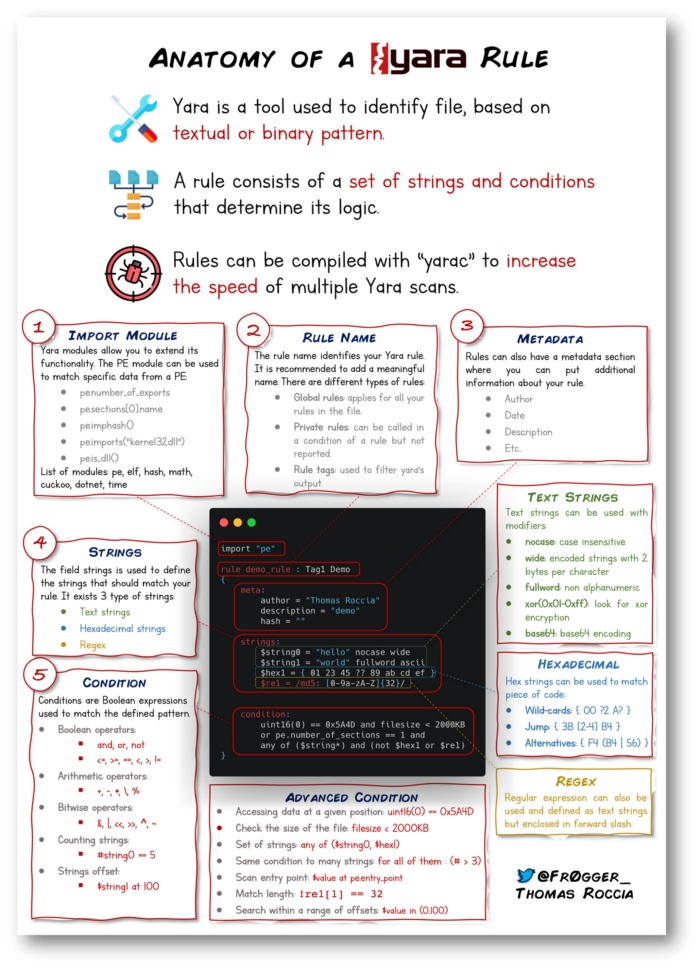
YARA and its rules are a way of identifying malware (or other files) by creating rules that look for certain characteristics. It was developed with the idea to describe patterns that identify particular strains or entire families of malware. Each rule has to start with the word rule, followed by the name or identifier. The identifier can contain any alphanumeric character and the underscore character, but the first character is not allowed to be a digit. Rules are composed of several sections.The condition section is the only one that is required. This section specifies when the rule result is true for the object (file) that is under investigation. It contains a Boolean expression that determines the result. Conditions are by design Boolean expressions and can contain all the usual logical and relational operators. You can also include another rule as part of your conditions. To give the condition section a meaning you will also need a strings section. The strings sections is where you can define the strings that will be looked for in the file.
There are several types of strings you can look for: - Hexadecimal, in combination with wild-cards, jumps, and alternatives. - Text strings, with modifiers: nocase, fullword, wide, and ascii. - Regular expressions, with the same modifiers as text strings.
Metadata can be added to help identify the files that were picked up by a certain rule. The metadata identifiers are always followed by an equal sign and the set value. The assigned values can be strings, integers, or a Boolean value. Note that identifier/value pairs defined in the metadata section can’t be used in the condition section, their only purpose is to store additional information about the rule. Data to look for: • meaningful domain names or IP addresses that the malware may connect out to • filenames that the malicious file references • any unusual API calls that the files reference • various version numbers inside the malware • any registry value that the malware references.
Yara Rule Generators
Yara Rule Testing Tools
arya - Arya is a unique tool that produces pseudo-malicious files meant to trigger YARA rules. You can think of it like a reverse YARA.
Resources
https://github.com/EFForg/yaya - Automatically curate open source yara rules and run scans
https://yaraify.abuse.ch/ - YARAify is a project from abuse.ch that allows anyone to scan suspicious files such as malware samples or process dumps against a large repository of YARA rules. With YARAhub, the platform also provides a structured way for sharing YARA rules with the community.
YaraHunter - Deepfence YaraHunter scans container images, running Docker containers, and filesystems to find indicators of malware. It uses a YARA ruleset to identify resources that match known malware signatures, and may indicate that the container or filesystem has been compromised.
Writing Yara Rules
Yara Training
Operator Handbook: YARA - pg. 428
Last updated